EASD Exploiting ASDM Vulnerabilities and Proactive Defense Strategies Against Sophisticated Malware in Cisco ASA Firewalls Security
Main Article Content
Abstract
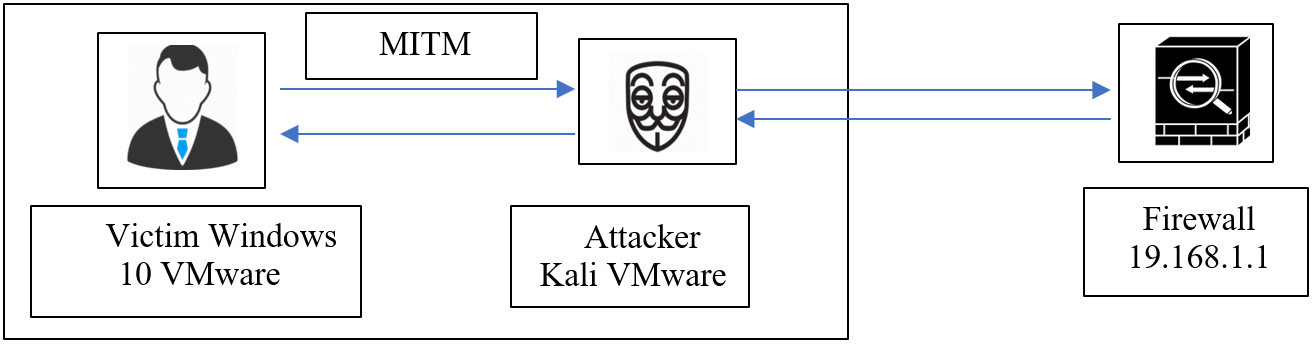
As cyber threats continue to evolve in sophistication, this study investigates critical vulnerabilities within Cisco ASA firewalls, with a particular emphasis on the Adaptive Security Device Manager (ASDM) interface. The research demonstrates how advanced malware can exploit the file-based architecture of ASDM to circumvent traditional firewall protections. A controlled virtual environment was established using VMware, incorporating a native Cisco ASA 5512-X firewall running software version 8.6(1), a Windows 10-based victim machine, and a Kali Linux attacker system. To facilitate the exploitation process, substantial modifications were applied to the open source tool “theway”, enabling it to extract and reassemble the .bin installation package without altering the structure of its internal components. Additionally, 7-Zip was employed to unpack the embedded .msi installer files, allowing for the insertion of malicious payloads. The WiX Toolset, used in its unmodified state, was then utilized to rebuild the .msi packages. These .msi files were selected as the primary attack vector due to their broad compatibility across ASDM versions and reduced likelihood of detection. In contrast, attempts to inject unsigned Java .class files into the pdm.sgz archive were unsuccessful, as recent ASDM versions enforce strict digital signature verification. The attack scenarios simulated in this study included reverse shell injection and credential interception through a man-in-the middle (MITM) attack. Results revealed significant weaknesses in Cisco ASA’s file validation procedures and outbound traffic monitoring mechanisms. To address these issues, a comprehensive multi-layered defense strategy is proposed, incorporating SIEM/EDR integration, robust digital signature enforcement, and internal network segmentation. The findings of this research contribute to both academic and practical efforts to enhance the security posture of enterprise firewall deployments against sophisticated malware threats.
Downloads
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.