Survey of Intrusion Detection Techniques in Cloud Computing
Main Article Content
Abstract
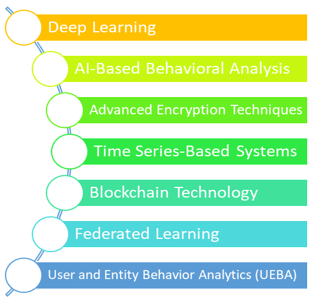
With the continued development of cloud computing environments, security measures have become more im-portant than ever. Intrusion detection systems (IDS) are considered one of the most critical security measures in cloud computing. Researchers aim to find effective technologies for detecting intrusions in cloud computing. This paper presents a comprehensive survey of the techniques used for Intrusion Detection in Cloud Computing and their classification. Specifically, it covers a range of techniques such as machine learning, and provides insights for researchers looking to develop more flexible and effective techniques for intrusion detection in cloud computing.
Downloads
Article Details

This work is licensed under a Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License.